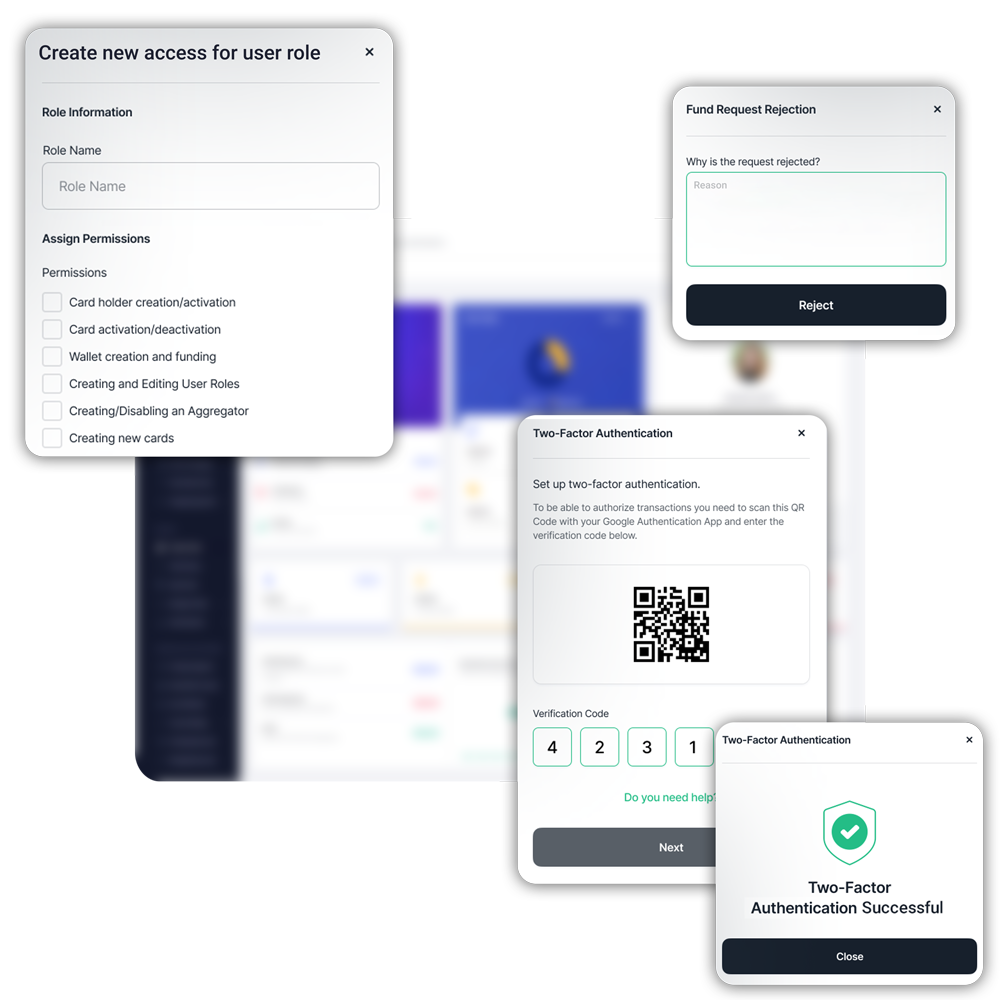
Secure your transactions
- Ensure PCI DSS compliance for increased payment protection
- Encrypt critical financial information of customers with SSL certificate
- Create tailored processes to avoid the storage of unwanted customer payment data
- Implement tokenization and encryption to mitigate payment risks
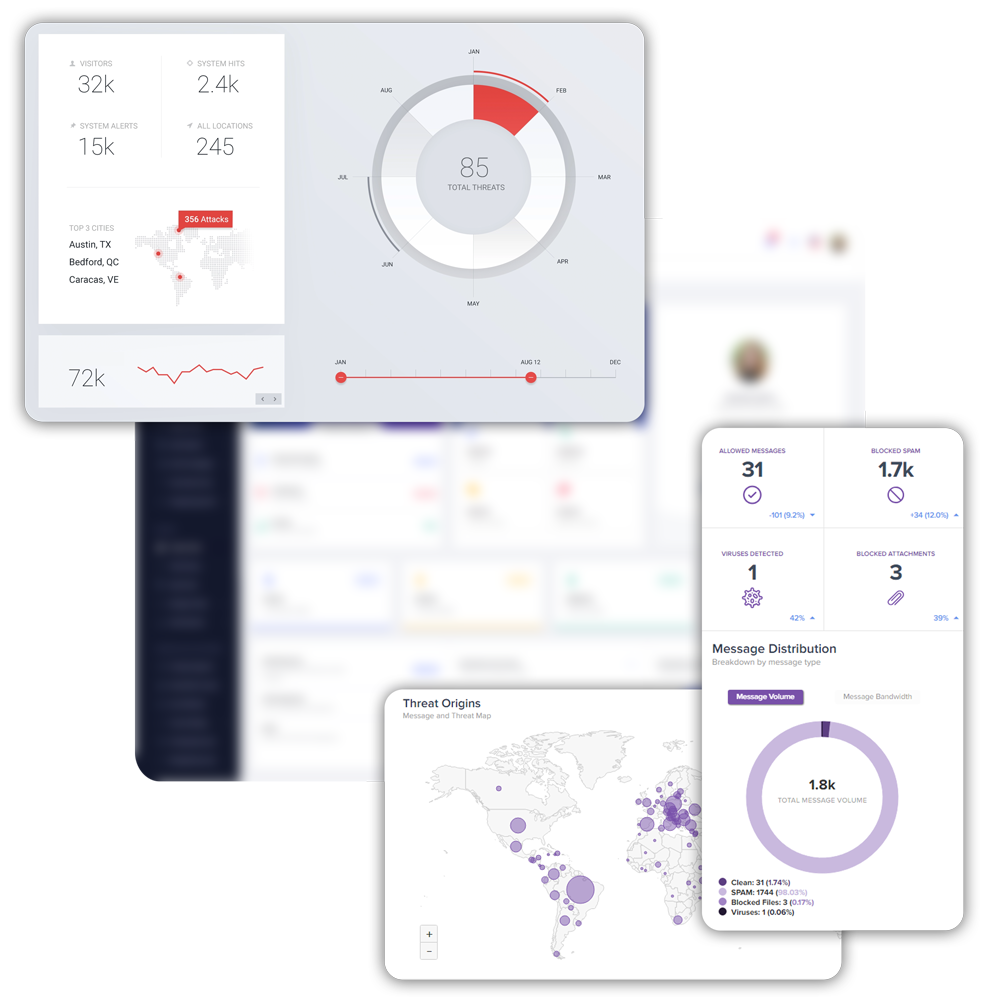
Protect your data
- Implement micro-segmentation for improved data protection and lowered risks
- Understand data lifecycle of sensitive data and employ continuous data monitoring
- Ensure compliance monitoring to align data policies to industry and regulatory standards
- Analyze data patterns to identify disruptions and malicious activities
- Ensure data storage security with regular backup of your entire data both in physical and cloud locations
- Conduct regular data audits to get complete visibility of potential breaches or threats

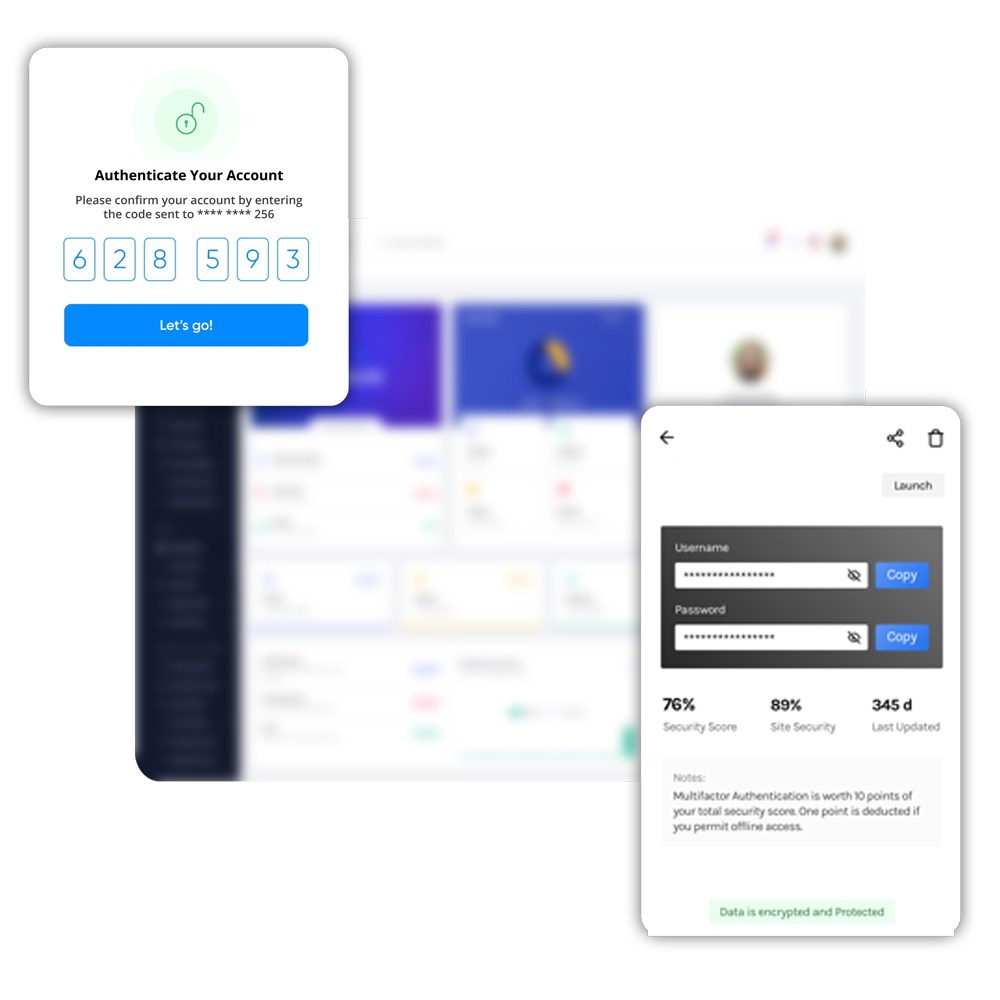
Access management
- Allow minimum access privileges to users and systems
- Eliminate the risk of attacks with advanced authentication methods such as MFA, tokens, and certificate-based authentication
- Monitor temporary accesses and automatically suspend them after the stipulated time
- Keep updating access credentials with new security questions, passwords, and encryption keys
- Implement meticulous access control mechanisms

Securing your network
- Identify potential access points with strict monitoring of incoming and outgoing traffic
- Set network access and download permissions to mitigate breaches
- Generate automated security prompts in regular intervals to change passwords and other access authentications
- Audit your networks regularly and run an automated check on security controls
- Isolate and segment networks to contain breaches in real-time

Build a trust framework
- Establish a zero trust architecture across networks, data, applications, and user accounts
- Ensure real-time trust verification and access management
- Streamline IT policies with your organizational policies related to access rights and use of personal devices
- Identify your endpoints and implement complete protection against malware, ransomware, phishing, XSS, and DDoS attacks

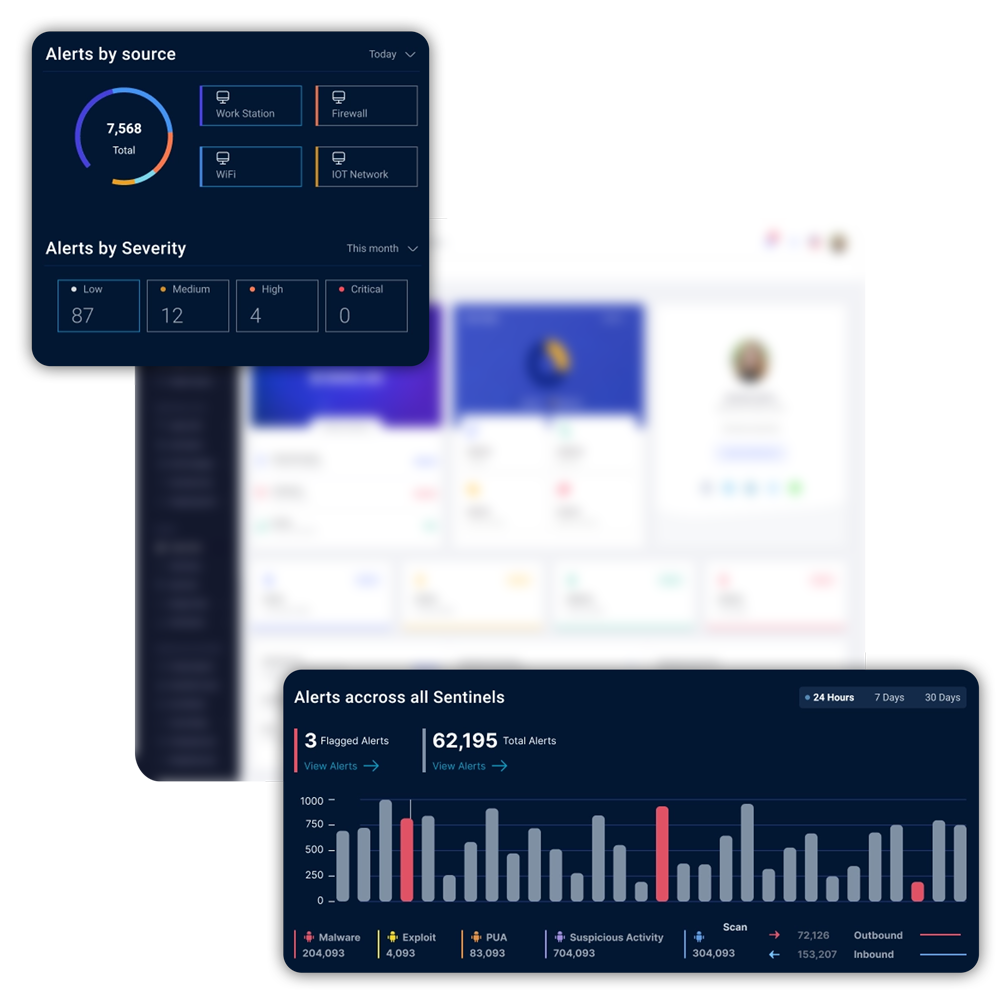
Analyze threats in real-time
- Run regular vulnerability assessments on databases, networks, and applications
- Identify potential vulnerabilities with automated vulnerability detection and mitigation
- Ensure regular patching of your software and systems
- Filter out malicious visitors, requests, and access such as SQL injections, Cross-site scripting, malware, and similar cyber threats

Detect system vulnerabilities to secure your business, customers and distributors against exploitation
Get Live DemoCustomer security
- Protect customer data across devices with multi-factor authentication and encryption practices
- Limit access to customer data based on user roles
- Perform data audits to automatically remove unwanted or unused customer data from your system
- Stay compliant with customer data policies such as GDPR and CCPA
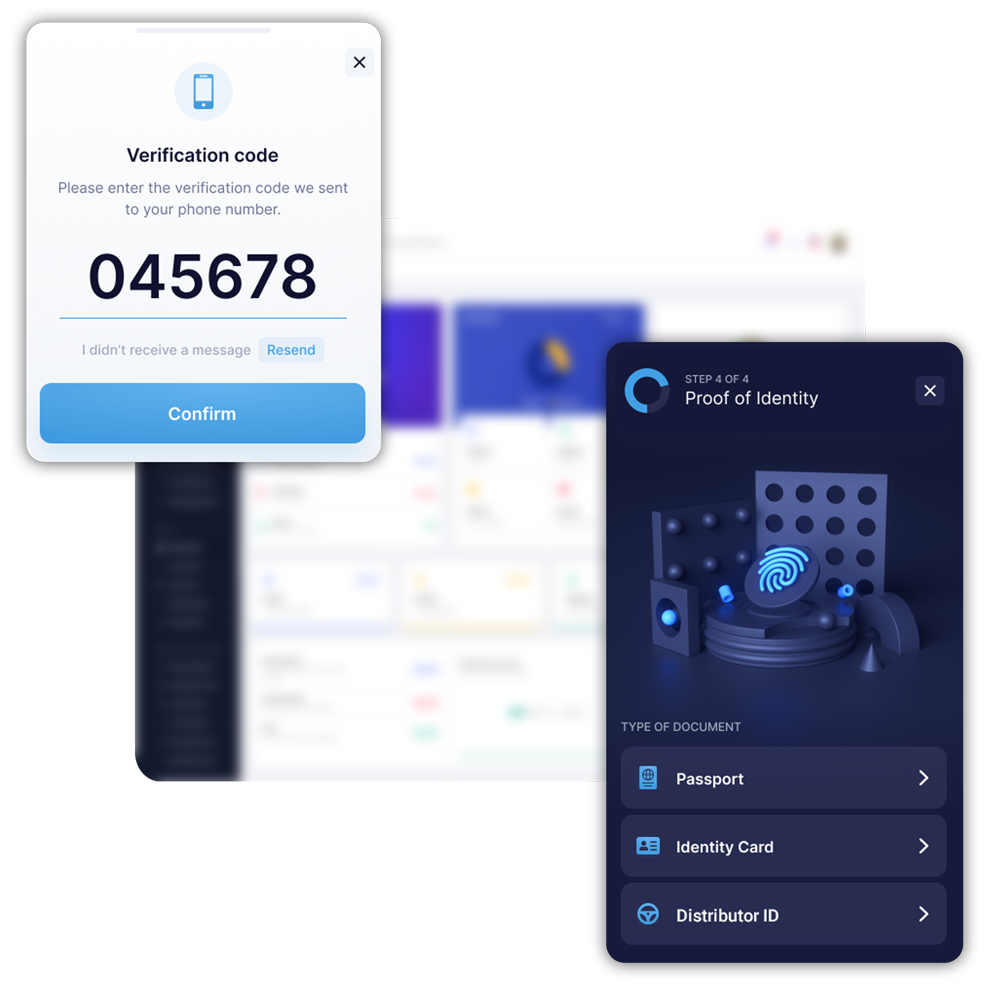
Design an incident response plan
- Run regular threat assessments including hardware and software devices
- Identify corporate mobile assets and keep them in the assessment loop
- Contain the threat in real-time with incident response tools
- Conduct tabletop exercises, penetration tests, and cyber threat simulations
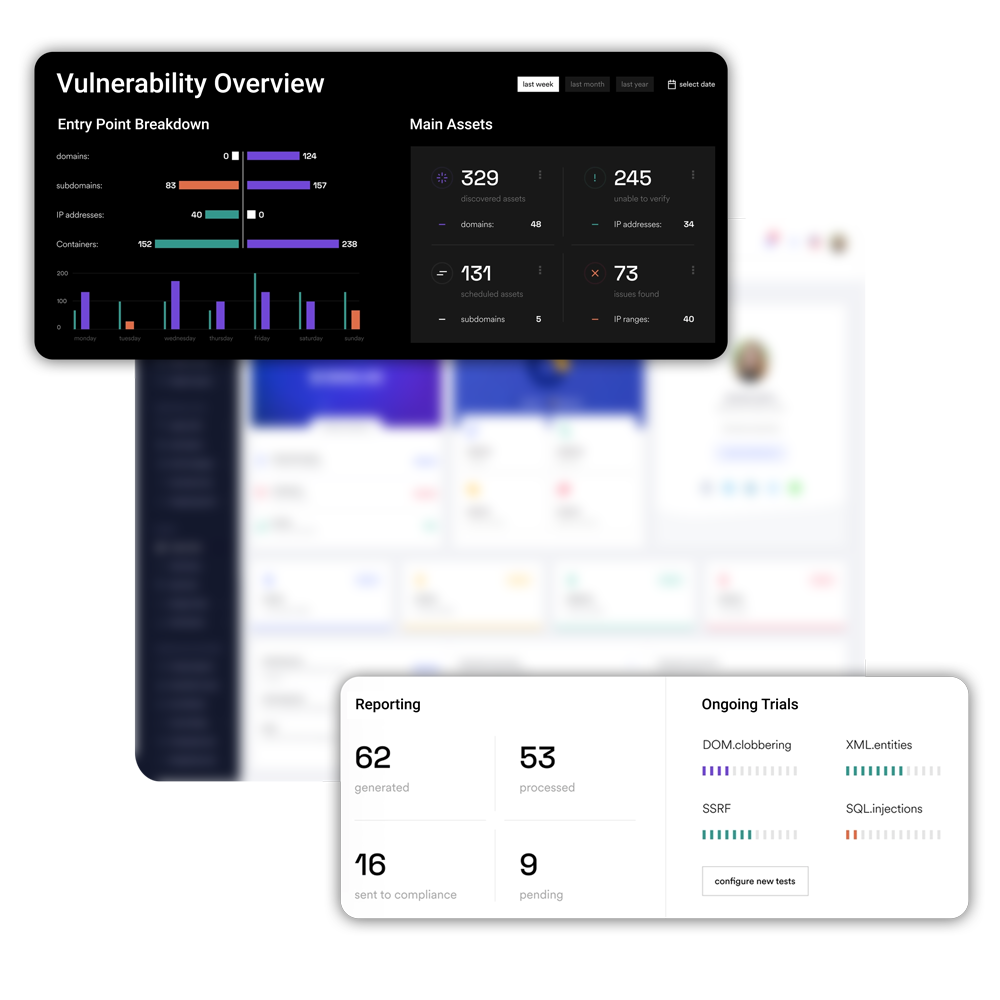
Disaster recovery
- Implement Firewalls and VPNs to gain complete control over your network and traffic
- Establish and maintain alternative data channels to retrieve lost data
- Reduce downtime with automated data backups
- Track your recovery metrics for optimizing your incident response and recovery plan
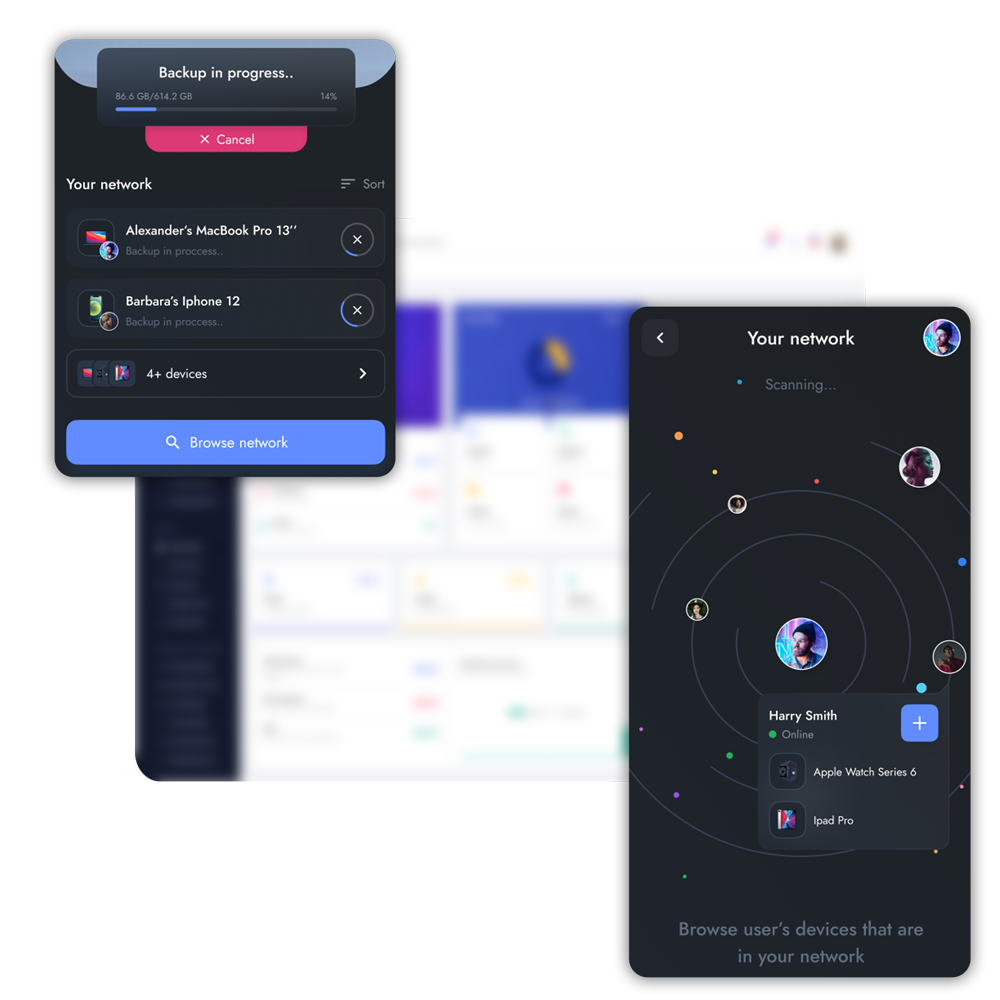
Establish a threat intelligence framework
- Develop intelligent defense mechanisms with data-backed threat decisions
- Build predictive capability to identify and notify in the event of threat incidents
- Design a proactive cyber intelligence framework to detect and protect your organizational and user data
- Respond faster to breaches and threats
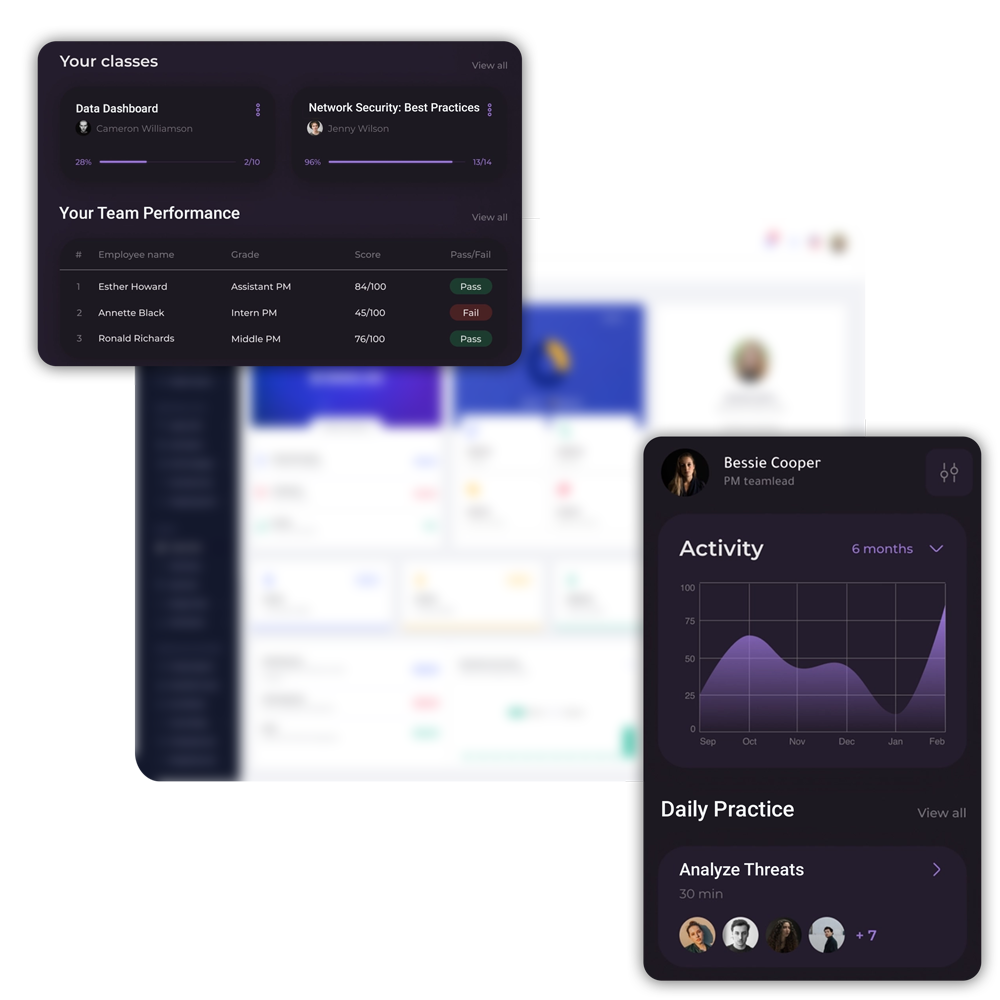
Educate your team
- Create cyber awareness with online training sessions
- Gamify your security training sessions with mock threats and cyber attack scenarios
- Schedule email campaigns and newsletters to inform them about new security advancements in the organization
- Track the effectiveness of your security awareness program with threat simulations




Ensure sustainable growth with the best security management practices
Get Live DemoCase Studies and Success Stories
Read from our customers how we have been helping MLM organizations stay one step ahead of rising competition and customer expectations.
Epixel MLM Software Reviews
4.6/5 121 Google reviews
I have dealt with several MLM software companies with mixed results. However, with Epixel, not only do they understand the complexities of compensation plans better than most, but they also build their software with the 'end in mind', meaning that they place a high importance on scalability and security.